What is Web Proxy?

An Introduction to Web Proxy
Understanding the function of web proxies is crucial in the current digital environment, when consumers’ top concerns are security and privacy online. Web proxies act as go-betweens for users and the internet, directing traffic via their servers to add an extra layer of protection and anonymity. This article will explore the idea of web proxies, including how they operate, their advantages, the many kinds of them, how to set them up, the dangers and concerns involved, and how they vary from VPNs. Let’s examine each facet one by one.
What is Web Proxy?
A web proxy is essentially a server that stands in between a user’s device and the internet. Through a web proxy, a user can request access to a website, and the proxy server acts as the user’s representative by forwarding the request to the intended website. By using this method, the user’s IP address and other personally identifiable information are successfully hidden from the website they are visiting. Web proxies are well-liked tools for getting access to blocked content and protecting online activity because they offer a degree of anonymity and privacy by hiding the user’s identity.
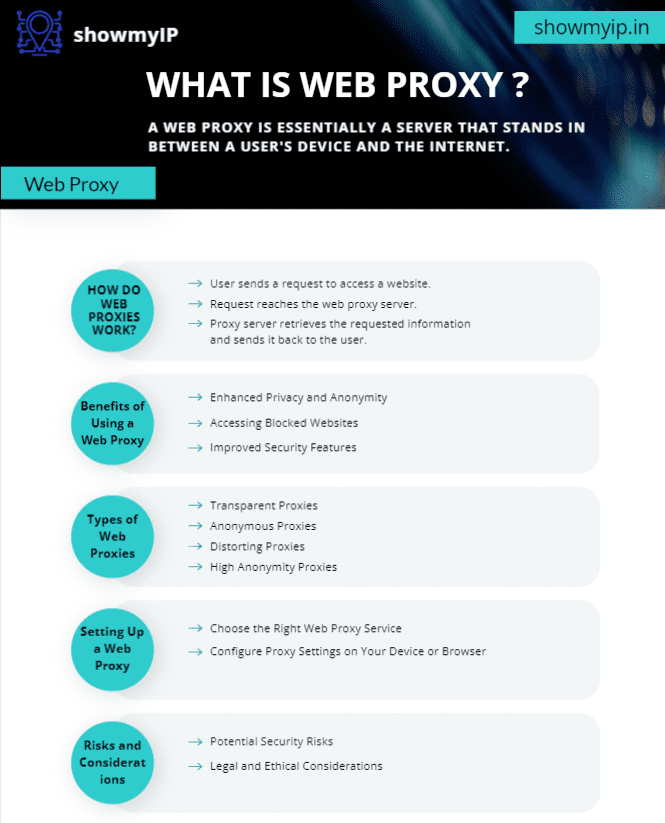
How Do Web Proxie Work?
A web proxy’s function is to intercept user internet requests and redirect them to the intended server. The web proxy server receives requests from users to visit websites first. After processing the request, the proxy server gets the needed data from the destination server and gives it back to the user. The user’s identity is essentially concealed from the target server throughout this procedure by substituting the proxy server’s IP address for the user’s. Through the proxy server, users may browse the internet safely and anonymously thanks to this technique.
The Benefits of Using a Web Proxy
Enhanced Privacy and Anonymity
The increased privacy and anonymity that a web proxy provides is one of its main advantages. Web proxies shield users’ IP addresses from websites so they can’t identify or follow their online activities. Users that want to get around geo-restrictions or are worried about their online privacy will find this anonymity very helpful.
Accessing Blocked Websites
With the use of web proxies, users may visit websites that might otherwise be inaccessible in their area or by their internet service provider. However, users should be cautious when using proxy servers located in different countries to ensure Proxy safety and privacy.
Improved Security Features
Web proxies provide enhanced security features in addition to privacy and accessibility advantages. Web proxies frequently come with built-in security features like ad blocking, virus detection, and encryption to shield users from online dangers and objectionable content.
Types of Web Proxies
Transparent Proxies
Transparent proxies do not conceal the IP address of the user or alter their request. Rather, they reduce bandwidth utilization and enable speedier access to websites that are often visited by caching web information.
Anonymous Proxies
Anonymous proxies offer a greater degree of privacy and anonymity by hiding the user’s IP address from the websites they visit. They might nevertheless, however, provide the target server with some identification information about the user.
Distorting Proxies
By giving the destination server a fake IP address, distorting proxies give the impression that the request is coming from a different place. This contributes to the user’s identity and location being further hidden.
High Anonymity Proxies
The greatest degree of privacy and anonymity is provided by high anonymity proxies, which conceal from the target server any information pertaining to the user’s identity, including their IP address. For those who want the highest level of security and anonymity, these proxies are perfect.
Setting Up a Web Proxy
Choosing the Right Web Proxy
Before setting up a web proxy, it’s essential to choose the right proxy service that aligns with your privacy and security needs. Consider factors such as server location, encryption protocols, and user reviews when selecting a web proxy provider.
Steps to Configure Your Web Proxy
Once you’ve chosen a web proxy service, the next step is to configure it on your device or web browser. This typically involves accessing the network settings or proxy configuration options and entering the details provided by your chosen proxy service, such as the proxy server address and port number.
Risks and Considerations
Potential Security Risks
Web proxies have many advantages, but there may be security hazards as well. Proxy servers may be used to log users’ internet activities, expose users to malware and phishing scams, and send sensitive data via insecure connections, among other things
Legal and Ethical Considerations
Users should also think about the ethical and legal ramifications of utilizing web proxies, especially in areas where such use may be prohibited or controlled. When web proxies are used improperly to break the law or evade copyright regulations, there can be dire repercussions.
Web Proxy vs. VPN: Understanding the Difference
Understanding the differences between virtual private networks (VPNs) and web proxies is crucial for comprehending their different uses and functionality. Web proxies just encrypt web browser traffic; in contrast, VPNs encrypt the user’s complete internet connection, providing a better level of security even though both technologies offer privacy and security benefits.
The Future of Web Proxies
Web proxies are predicted to play a more important role as long as consumers’ concerns about internet security and privacy remain high on the global user agenda. Future advancements could provide users even more control over their online actions through better security measures, integrated privacy features, and integration with other privacy-enhancing technology.
Conclusion
To sum up, web proxies are essential for improving security, preserving online privacy, and granting access to content that is forbidden. Users can utilize web proxies to secure their online activities by being aware on how they operate, the advantages they provide, the various varieties that are accessible, and the risks and considerations that come with using them. Web proxies are likely to continue to be useful resources for internet users looking to protect their security and anonymity online as long as technology develops and privacy concerns endure.
To confirm your IP address when using a proxy server, visit showmyIP.
FAQs
A web proxy serves as a middleman for your web requests, providing anonymity and unencrypted access to information that is restricted, while a VPN encrypts your entire internet connection and offers more extensive security measures. These are the primary distinctions between the two services.
Web proxies don’t make you totally anonymous, even though they can greatly improve your privacy by encrypting your requests and masking your IP address. Cookies, browser fingerprinting, and possible proxy server logging are just a few of the variables that can still compromise your online privacy.
Indeed, there are security dangers associated with utilizing free web proxies. These hazards include the possibility of malware exposure, phishing attempts, and the proxy server recording your online activities. Selecting trustworthy and safe proxy services is crucial.
Usually, configuring a web proxy entails adjusting your network configuration to direct all internet traffic via the proxy server. Usually, you may accomplish this through the network settings on your operating system or in the web browser settings.
Yes, one advantage of utilizing a web proxy is that it lets you access content that could be blocked in your area by using an IP address from somewhere else to conceal your true one. On the other hand, some services might have safeguards in place to identify and prevent proxies.

16 Responses
https://o-tendencii.com/
Have you ever thought about adding a little bit more than just your articles?
I mean, what you say is important and everything.
However think about if you added some great pictures or video clips to
give your posts more, “pop”! Your content is excellent but with images and videos,
this site could undeniably be one of the most beneficial in its field.
Amazing blog!
It’s difficult to find experienced people for this topic, however, you seem like you know what you’re talking about!
Thanks
quisquam sit inventore voluptas omnis suscipit repellat consequatur dignissimos totam alias voluptates quia. praesentium quos aspernatur consequatur delectus et ea consequatur repellendus incidunt reiciendis beatae corrupti debitis qui. provident enim ipsa temporibus libero rerum nobis ex sed consequatur deserunt accusantium vitae corporis.
enim inventore dolorem nesciunt facere beatae sapiente aut aut earum suscipit ducimus dolores magnam debitis. itaque est rem minus molestiae amet accusamus itaque distinctio consequatur necessitatibus. ipsum dolores doloribus deserunt non tempora quo vero totam dignissimos similique exercitationem qui dolorem cum maxime voluptatum eveniet eum sit. aperiam exercitationem eum voluptatibus possimus ipsam autem suscipit sunt repudiandae.
[url=http://happyfamilymedicalstore.online/]canadian pharmacy world coupon[/url]
[url=https://happyfamilystorerx.online/]low cost online pharmacy[/url]
voluptas non est eum dolor consequatur dolor voluptatum tenetur iste et corrupti id nemo. non aspernatur ratione repudiandae quas voluptatem aliquid ut atque sint sed dolorem aut repudiandae assumenda fugit eaque aut debitis maiores debitis. voluptate voluptatem at minima corporis molestiae aliquam sit unde. quo rerum beatae libero consectetur nihil debitis ullam possimus qui nostrum iste explicabo. delectus recusandae neque fugit provident dolores fugiat cum ad qui unde possimus similique.
[url=https://happyfamilystorerx.online/]canadian pharmacy 365[/url]
[url=http://modafinile.com/]provigil 400 mg[/url]
Greetings! This is my first visit to your blog!
We are a group of volunteers and starting a new project in a community in the same niche.
Your blog provided us valuable information to work on. You have done a wonderful job!
Thanks for sharing your thoughts about wordpress music player.
Regards